Here's why podman is more secured than Docker - DevSecOps
Here's why podman is more secured than Docker - DevSecOps
Here’s why podman is more secured than Docker - DevSecOps
We all know that Docker is one of the popular tool for containerizing an application in devops world.
but, In this article we will see about podman and why it is more secured way to run container.
Podman is a daemonless container engine for developing,managing and running container in linux system.

Audit Logging
Linux system stores the user account information in a file called /etc/shadow. it is a common security file to watch in a linux systems.
Linux kernel allows administrators to watch for the processes that modifies the file and keep a record of it in audit.log.
administrators wants to know if any process modifies the file from the log.
auditctl -w /etc/shadowthis command will add the /etc/shadow file to the audit system.
let’s modify the /etc/shadow file and see what happens
touch /etc/shadowausearch -f /etc/shadow -i -ts recent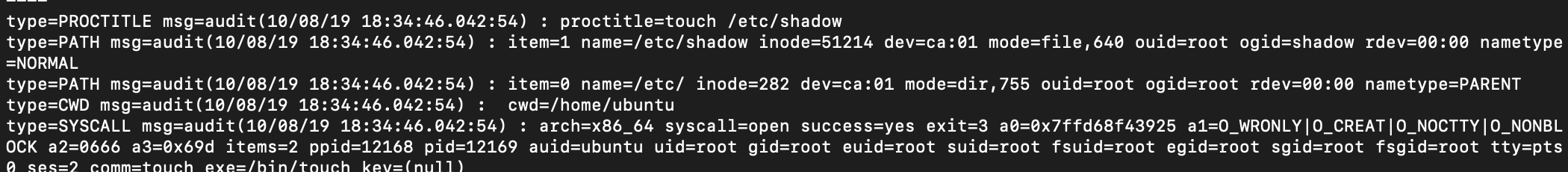
audit record will show lots of information about the process and owner of the process audit UID(auid) who modified the /etc/shadow file
Login UID in linux kernel
there is a file called loginuid stored in /proc/self/loginuid. this file is a part of proc structure in linux. this file can be set only once.
after it is set, the kernel will not allow any process to reset it.
When I log into the system, the login program sets the loginuid field for my login process.

My UID was 1000.
Even if i change to root, my loginUID will be the same. 1000
Important thing to note here is that every process that fork and execute from the initial process will have the same loginuid.that is how kernel knew about the user information.
How it works in containers
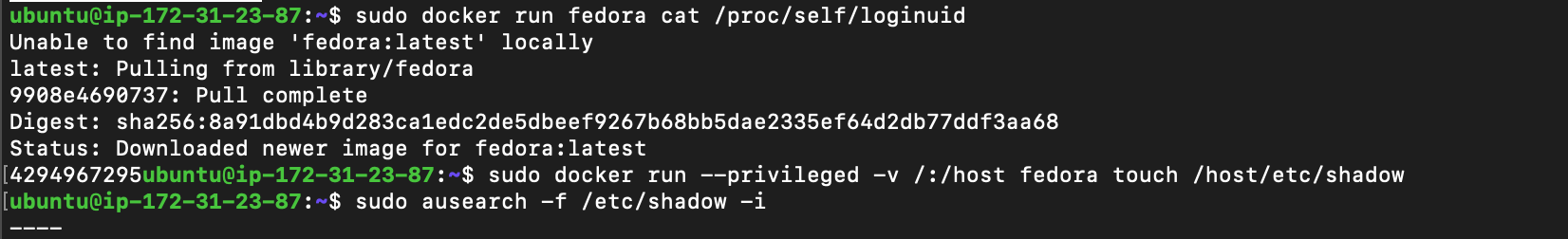
let’s try to run the same process in podman and docker containers
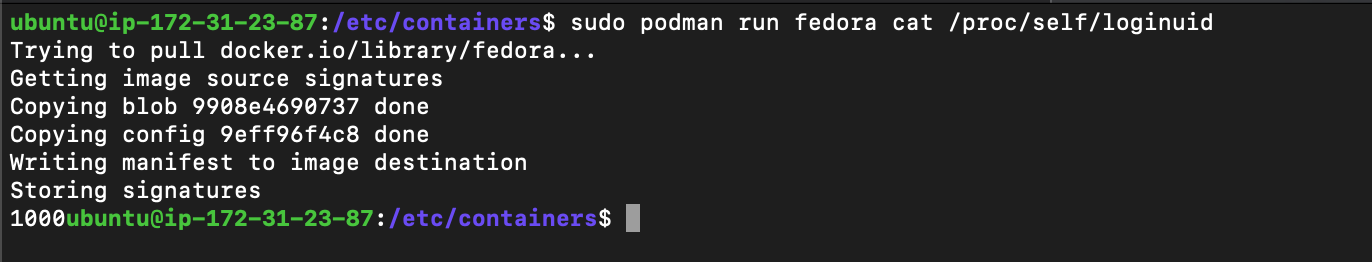
Now, we will check it with docker
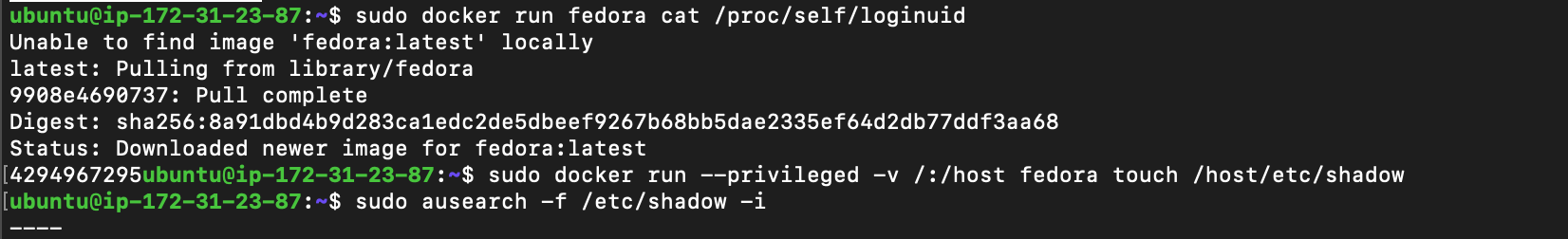
Hmm, Interesting… why is the loginuid is different for docker and same for podman.
The Reason
So, if you remember carefully. i said some important keyword called fork and execute. let’s discuss about it here .
podman uses a fork/exec model for the container, So the container process is the child of podman process. whereas, docker uses a client/server model.
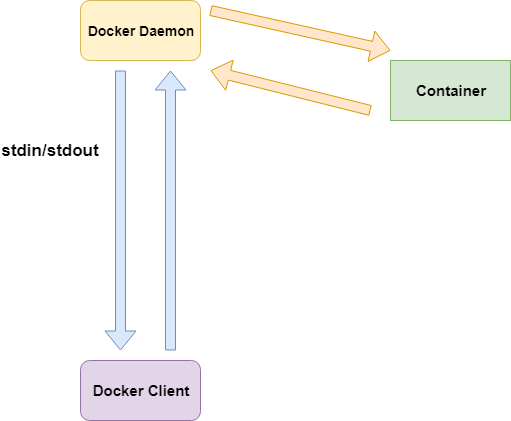
docker uses a cli which communicates with docker daemon via a client/server operation.
Then the docker daemon creates a container and handles communications of stdin/stdout back to the docker client tools.
So the default loginuid of podman container still the same(1000) whereas, docker default loginid of processes(before their loginuid is set) is 4294967295.
Since the container is an child of the docker daemon and docker daemon is the child of init system.
What could go wrong?
Let’s see what happens if a container process created by docker modifies the /etc/shadow file.
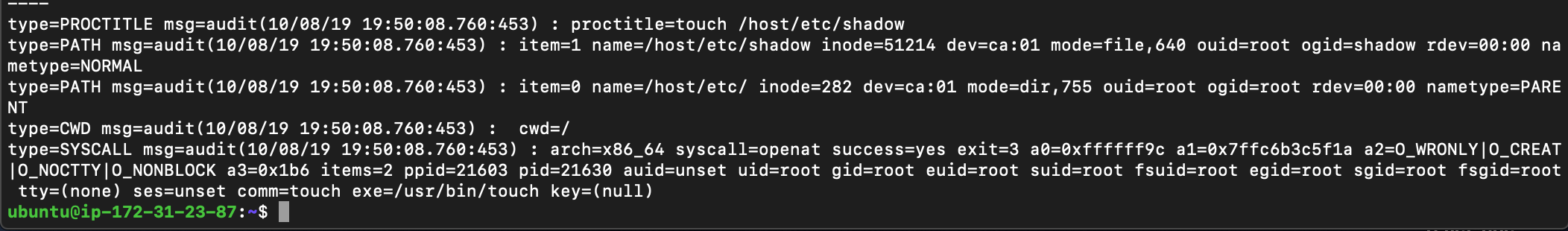
you can see the uid as unset in the case of docker. this means the administrator will know that the /etc/shadow is modified . but, admin will never know who modified that file.
if that hacker removes the docker container, then there would be no trace on the system of who modified the /etc/shadow file.
Now, Let’s look at the exact same scenario for Podman.
sudo podman run --privileged -v /:/host fedora touch /host/etc/shadowsudo ausearch -f /etc/shadow -i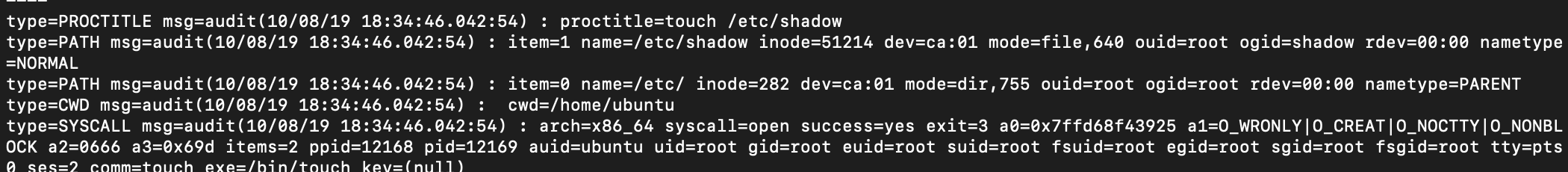
Podman records the process which modifies the file correctly since it uses traditional fork/exec model.
Here’s why podman is more secured than Docker - DevSecOps. Using Podman for launching containers allows you to maintain better security though audit logging.
The auditing system is very powerful for watching what processes do on a system.
Reference : https://opensource.com/article/18/10/podman-more-secure-way-run-containers
